When employees work from an office it is easier to manage the environment as it is consistent and has more defined boundaries. One of the main challenges businesses have faced over the past 18 months of remote and hybrid working has been how to maintain a strong security structure whilst employees are not actually in the office. Employees working from home increases the risk of cyberattacks enormously.
For businesses that are wanting to improve their security posture whilst remote or hybrid working there are many solutions that can be put in place, however few are as effective and comprehensive as moving workloads to the cloud with Azure Virtual Desktop (AVD).
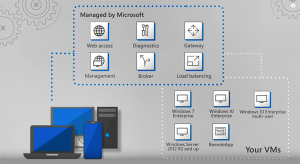
What is Azure Virtual Desktop?
AVD is a solution that is deployed through Azure and allows users to access all applications from anywhere on any device. AVD helps to increase flexibility, reduce costs and improve the business’ security posture. Below are 6 ways AVD can improve your businesses security.
Baseline Images
When a IT administrator is setting up AVD, they can start by creating a golden image. This a pre-configured computer template for all users with AVD. A golden image includes all necessary applications, security implementations and user settings. A major security challenge that many businesses may face is when users install applications or services without the consent of the IT department. This increases the risk of an attack as the IT department may not be aware of the applications that are being installed, therefore they can not ensure they are secure. Using golden images reduces this risk as the only applications on the virtual machine are the ones that were pre-configured from the beginning.
Updates and Patch Management
An easy method to improve security posture and reduce the risk of an attack is to keep all systems and apps up tp date and run patches as soon as possible. This may seem simple in theory, however, many users will delay updates – especially if it means they have to restart their machine. If these patches fix security flaws, delaying the update could leave systems vulnerable to an attack. With AVD it is simple to update all VM’s at the same time to ensure all computers within an organizations are updated and secure. These updates can also be run outside of office hours to ensure that downtime is minimized.
Timely Recovery After an Attack
Malware attacks have been an ongoing threat for IT systems. This is where a piece of malicious software completes unauthorised actions on a users system. These attacks can be hard to recover from because most of the time the user cannot then access their system. Using VDI makes recovery more efficient. A golden image allows you to revert a VM back to when it want infected with malicious software. This simplifies disaster recovery and ensures business continuity, regardless of where employees are working.
Conditional Access Policies
Conditional Access is a tool used in Azure Active Directory to ensure only authorized users are accessing information and systems. It means that if a user wants to access a resource, they must complete an action. An example of this could be multi-factor authentication to ensure it is not a threat actor trying to access personal information.
Hosted on Azure
One of the key security benefits of running a VDI solution on Azure, is the fact that Microsoft is extremely security conscious. Everything within the Azure environment is automatically encrypted and has sophisticated detection methods to prevent many cyberattacks. Microsoft also has over 3,500 cybersecurity experts who work on your behalf 24/7 to ensure all workloads hosted on the Azure cloud stay secure.
Intelligent Defenses
With Azure Virtual Desktop it is possible to identify threats with real-time cybersecurity intelligence. The Microsoft Intelligent Security Graph gives actionable insights based off machine learning, behavioral analytics, and application-based intelligence. This greatly improves a business’s security posture as it constantly monitors usage to discover anomalies before it is too late.


 Previous
Previous








